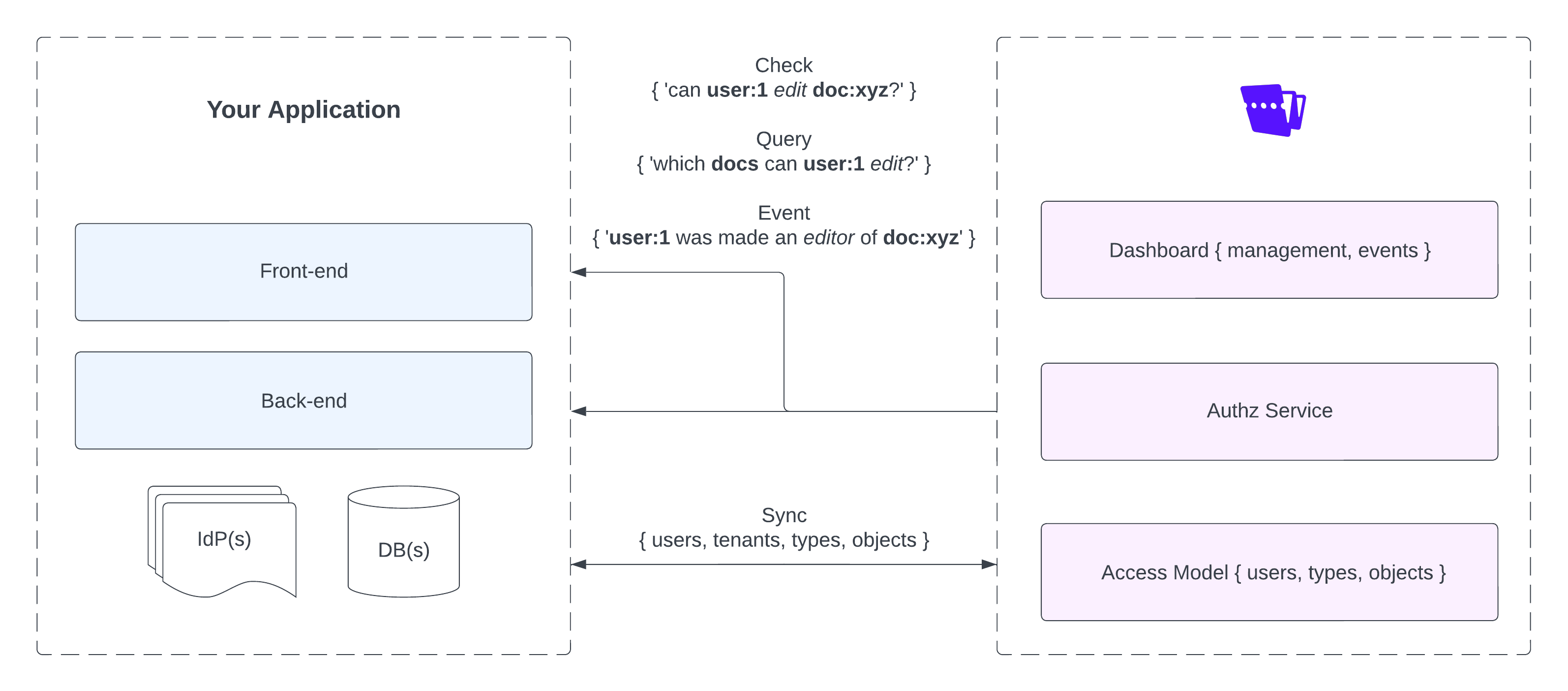
Overview
Warrant is a combination of cloud hosted services, developer tooling, and infrastructure built to help product, engineering and ops teams implement and maintain robust authorization and access control in their software products. The system includes:
- A fully managed, globally distributed, highly-available, high performance authorization service
- A fully managed administration dashboard
- A suite of developer tooling & infrastructure
Admin dashboard
The Admin Dashboard sits in front of our core API, serving as a central control panel for Warrant. The dashboard provides an easy way for product, engineering, and operations teams to manage their authorization model & policies, audit & track realtime access to their system, configure account settings, and much more.
Authorization service
Warrant's authorization service is a fully managed and distributed cloud service based on Google's Zanzibar Global Authorization System. Like Zanzibar, users model their authorization scheme by defining a schema using object types and relations and create warrants (also known as ACLs - or tuples in Zanzibar) against that schema. Warrants are queried against to perform runtime access control checks. All read and write operations (including access checks) are exposed via API.
Access model
As mentioned above, Warrant's authorization service is based on Google Zanzibar and composed primarily of object types and warrants (ACLs/tuples). Object types define the key objects in a system (ex. role, permission, report, document, folder etc.) and the relationships that can exist between instances of each type. Object types and their attributes are described in more detail here. By default, Warrant ships with a core set of built-in object types that make it easy to implement common authorization schemes like role based access control. You can read more about these built-in types here.
While object types define an overall authorization scheme, warrants are the specific access rules that grant access to resources and dictate the results of access checks. For example, a system might have role, permission and user object types that enable role based access control. In this system, an example of a warrant could be [user:1] is a [member] of [role:admin]. Each warrant represents an authorization rule that refers to one of the system's object types. You can read more about warrants here.
Tools & Infrastructure
Warrant provides official SDKs for most popular back-end (Go, Node.js, Python, Java) and front-end (React, Vue, Next) languages and frameworks, making it easy to add authorization to any layer of the stack. The SDKs support all read and write operations on the authorization service including session-scoped authorization checks & UI components for client-side use.
Warrant also offers deep, 'plug-n-play' integrations for other complex but common authorization and access control use-cases such as self-service (or delegated) access management.
Identity & Authentication
It's important to note that Warrant is exclusively an authorization system. It is not an identity provider (IdP) and does not provide any authentication capabilities for your users. However, Warrant does integrate easily with any authentication provider (Auth0, Stytch, Okta etc.) or custom authentication implementation.
Follow one of our guides below to integrate Warrant with your authentication provider: